PR Status Check Enforcement
Like Snyk, Terracotta AI can enforce status checks right inside your pull request
Enforcing Checks in Pull Requests
Terracotta AI integrates directly into your pull request workflow as a set of automated, pre-merge status checks, helping you enforce policy, catch issues early, and prevent risky infrastructure changes from being merged, automatically.
How It Works
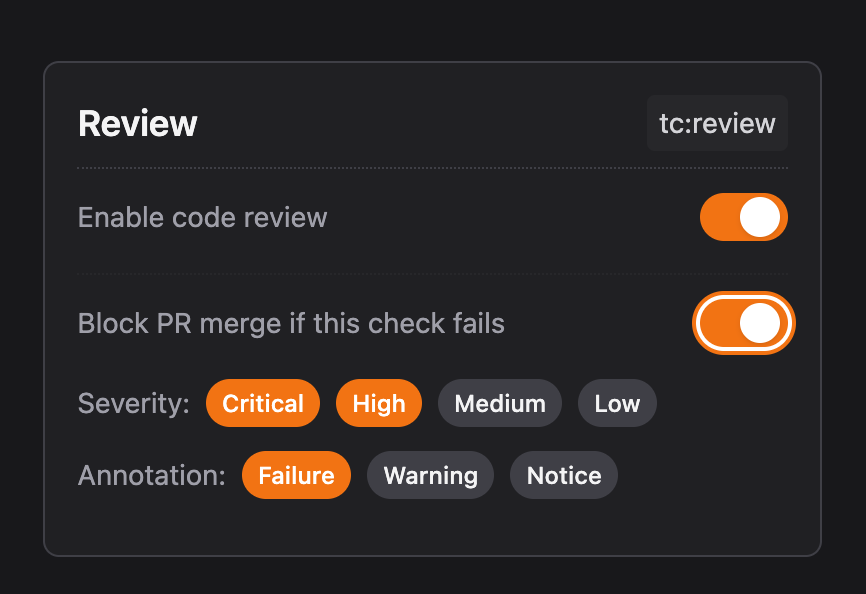
- Pull Request Checks
- Terracotta runs a suite of AI-powered checks on every pull request. Each command (e.g.,
tc:review, tc:drift, tc:cost, tc:conflict) is reported as a status check in GitHub or Bitbucket. These show up just like CI jobs or tests.
- Terracotta runs a suite of AI-powered checks on every pull request. Each command (e.g.,
- Merge Blocking
- You can configure your Git provider to require that Terracotta checks be passed before merging. If a check fails due to a critical issue like a high-risk IAM change, missing tags, or a cost spike, the PR is automatically blocked until it is resolved.
- Org-Wide Guardrails
- Apply consistent rules across all repositories and teams:
- Enforce max cost increases per PR or per resource type
- Require specific tags or naming conventions
- Prevent unsafe IAM permissions (e.g., * actions)
- Detect out-of-band changes or drift before they hit production
- Zero Additional Setup
- Apply consistent rules across all repositories and teams:
| Severity | Annotation | Blocks Merge? | Description |
|---|---|---|---|
| Critical | Failure | ✅ Yes | High-impact issues like exposed secrets, unsafe IAM policies, or security violations. |
| High | Failure | ✅ Yes | Serious misconfigurations or policy breaches. |
| Medium | Failure / Warning | ✅ / 🚫 | Can block if annotated as Failure. Otherwise, surfaced as a warning. |
| Low | Failure / Notice | ✅ / 🚫 | Can block if annotated as Failure. Otherwise, shown as informational. |
Real-World Example
When a developer opens a PR, Terracotta AI may automatically:
• Flag hardcoded secrets or misconfigured resources via tc:review
• Surface resource drift between code and cloud via tc:drift
• Estimate monthly cost increases via tc:cost
• Detect overlapping resources in parallel PRs via tc:conflict
If any of these checks fail based on your configured policies, the pull request will be blocked from merging.
Updated 3 months ago
